If you live in Indonesia or currently using Indonesian mobile number, you might have received an SMS from Ministry of Communication and Information Technology of Indonesia (Kemkominfo) about ransomware. The SMS warns people (especially IT manager) to prevent ransomware by deactivating the LAN/hotspot and backing up data to other storage.
This SMS is in response to WannaCry, a ransomware that attacked more than 230,000 computers in 150 countries on Thursday 11 May 2017. The attack spreads by multiple methods, including phishing emails and on unpatched systems as a computer worm. The ransomware first attacked Telefonica, a large telecommunication company in Spain, as well as parts of Britain’s National Health Service (NHS), FedEx, Deutsche Bahn and LATAM Airlines.
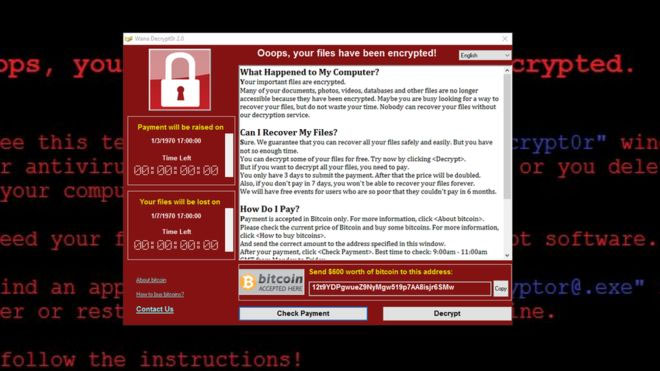
WannaCry (other name: WannaCrypt, WanaCrypt02 2.0, Wanna Decrypter) is a form of ransomware that locks up files on the computer (in this case is mainly computers with Windows XP operating system) and encrypts them in a way that you cannot access them anymore. The ransomware is believed to use the EternalBlue exploit, which was developed by the US National Security Agency (NSA).
When a computer is infected, a pop up window appears with instruction to pay for about $300 (the price increases over time) to regain the access. The ransom could only be paid in the form of bitcoin payment.
WannaCry has also spread in Indonesia. Rumah Sakit Dharmais in Jakarta is among the victims of WannaCry attack. Fortunately the hospital has always been backing up their data, so the impact can be minimized.
How to stay away from ransomware
The Ministry of Communications and Information Technology yesterday issued an official guide on how to prevent WannaCry from attacking your computers.

- Before turning on your computer/server, switch off hotspot/Wi-Fi and terminate any connections to LAN cable/internet.
- Immediately move data to devices running non-Windows OS (Linux or Mac OS), and/or back up/copy all data to a separate media storage.
- Deactivate Server Message Block (SMB) and macros functions.
The ministry also added some additional steps IT management within firms or organizations can take to protect entire networks from WannaCry, such as installing the MS17-010 patch on Windows computers and running up-to-date anti-virus software.
Since some of the attacks come in the form of phishing emails, the ministry also warned against opening email attachments or links unless one is sure of its contents. Beware of the emails containing invoices, job offers, security warnings, and other legitimate files.




